Blog
Security That Ships
Security, strategy, and developer-first thinking for teams pushing open-source forward.
This is some text inside of a div block.

Hopper Just Made Exploitability Verification Instant
Introducing Hopper Exploitability Verification. AI-driven analysis that confirms what is exploitable across your entire software ecosystem. Noise removed. Real impact verified.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
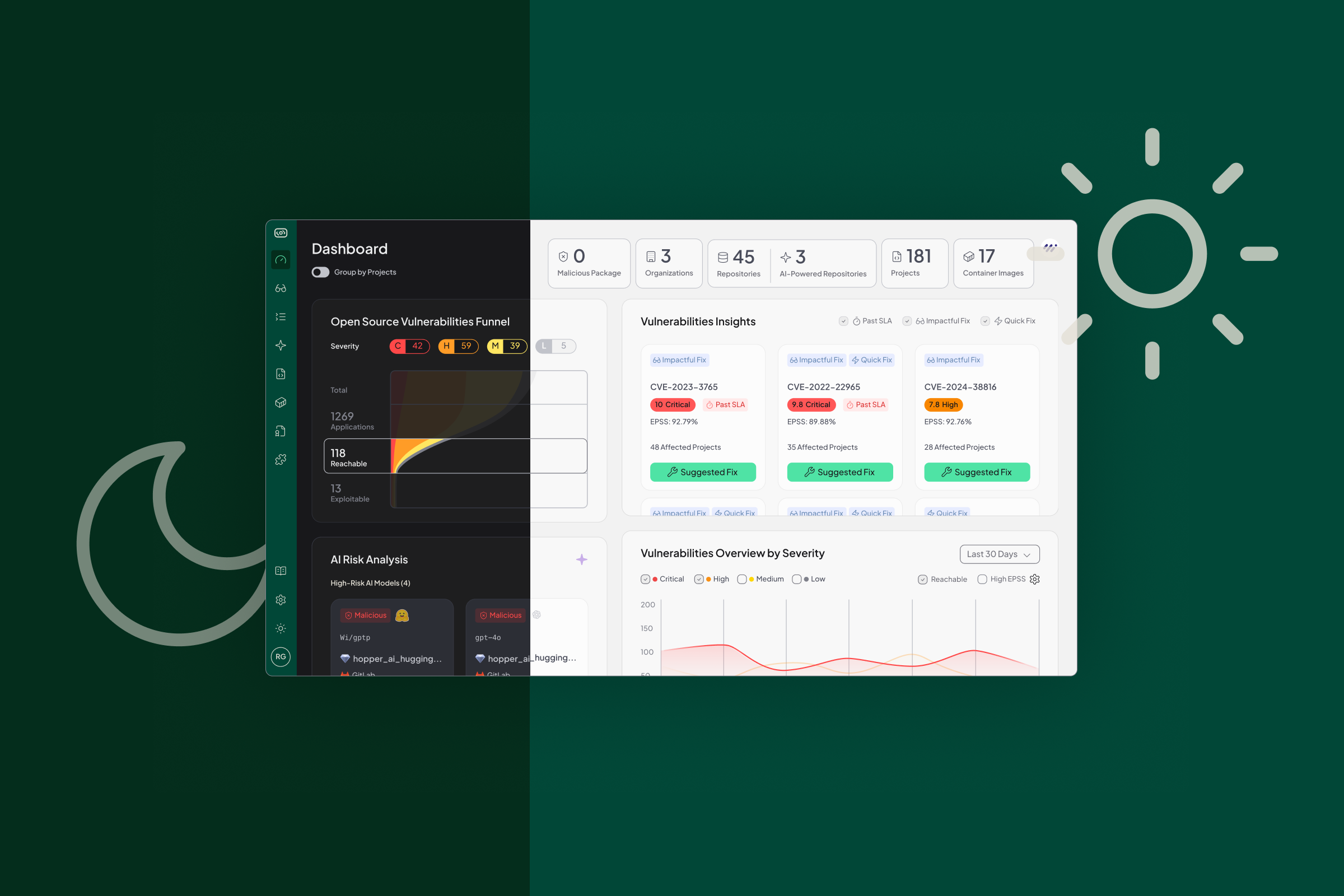

Brighten Your Workflow. Hopper Now Supports Light Mode.
Hopper now supports Light Mode, giving teams a brighter and more comfortable way to navigate open-source risk. Built to meet developers and security professionals where they are, this update brings more flexibility, personality, and ease to the Hopper experience.
Product


Hopper Just Made Exploitability Verification Instant
Introducing Hopper Exploitability Verification. AI-driven analysis that confirms what is exploitable across your entire software ecosystem. Noise removed. Real impact verified.
Announcements


Delivering Precision Container Security with Function-Level Reachability
Introducing Hopper’s latest product release: container reachability, a function-level analysis that separates real risk from noise across system and application layers in container images.
Product


SCA vs SAST: Two Different Tools for Two Different Problems
SCA vs SAST explained: Learn how Software Composition Analysis and Static Application Security Testing differ, their limits, and why modern teams need both.
Insights

How Hopper Sees AI as a Design Partner, Not a Replacement
How Hopper’s design team uses AI as a creative partner — not a replacement — to improve clarity, speed up iteration, and bring more humanity to product design.
Insights


The Vulnerability Noise Tax: What Security Really Pays for False Positives
Security teams spend millions each year managing vulnerabilities that don’t matter. This post breaks down the real cost of “security noise,” why it drains budgets and innovation, and how Hopper eliminates it through function-level reachability analysis.
Insights


Hopper for ASP.NET: Precision Reachability for the Microsoft Stack
Hopper extends its precision reachability analysis to ASP.NET, modeling DI, reflection, async, and generics to deliver accurate, noise-free security insights.
Product
.png)

Reachability in AppSec: What Each Type Really Tells You
Not all reachability is equal. The post explains how package-level, function-level, internet, and runtime reachability each shape AppSec accuracy and prioritization, and how Hopper combines them with exploitability and business context to cut 93% of noise and focus teams on real risks.
Insights


Hopper Recognized for Innovation and Growth in 2025
Hopper has been recognized as Innovation of the Year at the Cybersecurity Awards and Finalist in the AWS & CrowdStrike Cybersecurity Accelerator. These milestones highlight Hopper’s role in redefining application security by cutting through noise, reducing risk, and enabling enterprises to secure innovation without slowing down.
Announcements
Newsroom
Hopper Press Mentions and Releases
Visit Publication Article

September 15, 2025
In Praise of Resilience: Why We Invested in Hopper Security
-Logo.wine.png)
Visit Publication Article

September 4, 2025
The ART of Taming Agents: A CISO’s Framework for Managing Enterprise Risk in the Age of Agentic AI

Visit Publication Article

April 25, 2025
Hopper Uncovers Over 2.5 Million Vulnerabilities Hidden in Java

Visit Publication Article

April 22, 2025
Hopper raises $7.6M to accelerate software development with streamlined risk management
Visit Publication Article

April 22, 2025
Open Source Security Firm Hopper Emerges From Stealth With $7.6M in Funding

